Mehr Sicherheit für Kreditkartenzahlungen im E-Commerce mit 3-D Secure 2
Höherer Komfort für Ihre Kunden, maximaler Schutz für Ihr Business. Selbstverständlich zu 100 Prozent PSDII-konform.


Keine Conversion-Verluste, trotz 3-D Secure 2
Umgehen Sie 3-D Secure 2 für ausgewählte Transaktionen, indem Sie die Ausnahmen von der starken Kundenauthentifizierung (SCA) optimal nutzen: Individuelles und automatisiertes Handling von SCA Exemptions und Soft Declines im Computop Paygate.
Sie suchen Informationen zur technischen Integration von 3-D Secure 2?
Wie funktioniert 3-D Secure bisher?
Das seit dem Jahr 2002 bestehende, weltweit standardisierte 3-D Secure-Protokoll (3DS) bietet Händlern und Verbrauchern zusätzliche Sicherheit bei Kreditkartentransaktionen. Mit dem Verfahren verifizieren sich Onlinekäufer gegenüber ihrer kartenausgebenden Bank (Issuer) als rechtmäßiger Karteninhaber.
Im Gegensatz zu einem herkömmlichen Bezahlvorgang per Kreditkarte im Internet verlangt 3-D Secure einen zusätzlichen Sicherheits-Code. Auf diese Weise wird die missbräuchliche Verwendung von Kreditkarten deutlich erschwert.
Video: Strong Customer Authentication (SCA) in der Praxis
3-D Secure richtig steuern und Konversion gewinnen. Vortrag von Claudia Klein und Volker Wohlrab beim Digitalen Expertenforum 2021.
Wie unterscheidet sich 3-D Secure 2 vom bisherigen Verfahren?
Im Wesentlichen stellt 3-D Secure 2 eine Weiterentwicklung des bisherigen 3-D Secure-Protokolls dar. Mit jeder Bestellung per Kreditkarte werden fortan bis zu 100 Datenpunkte an den Issuer übermittelt; basierend auf diesen Datenpunkten führt der Issuer eine Echtzeit-Risikobewertung durch. Wird eine Transaktion hierbei als risikoarm eingestuft, kann sie direkt und ohne weitere Interaktion des Käufers autorisiert werden.
Besteht jedoch Betrugsverdacht, wird der Käufer durch eine zusätzliche Sicherheitsabfrage (z. B. mittels Push-TAN) zur erneuten Bestätigung seiner Identität aufgefordert. Die Risikobewertung läuft für den Käufer nicht wahrnehmbar im Hintergrund ab. Die Erfassung und Weiterleitung der nötigen Daten erfolgt sowohl über das Shop-Backend des Händlers als auch durch den Payment Service Provider (PSP), über den 3-D Secure 2 an den jeweiligen Shop angebunden ist.
Wann und weshalb wird 3-D Secure 2 eingeführt?
Erklärtes Ziel der Einführung von 3-D Secure 2 ist einerseits, den Anforderungen an die Strong Customer Authentication (SCA) gerecht zu werden und sie ab 2021 für elektronische Zahlungsverfahren als Standard zu etablieren.
Andererseits soll durch die Einführung auch die Kaufabbruchquote sinken: Durch die individuelle, datenbasierte Risikobewertung können Transaktionen in ca. 95 Prozent aller Fälle direkt und ohne weitere Käuferinteraktion freigegeben werden – ein Großteil der Käufe findet somit künftig ohne Eingabe eines 3-D Secure Codes statt.
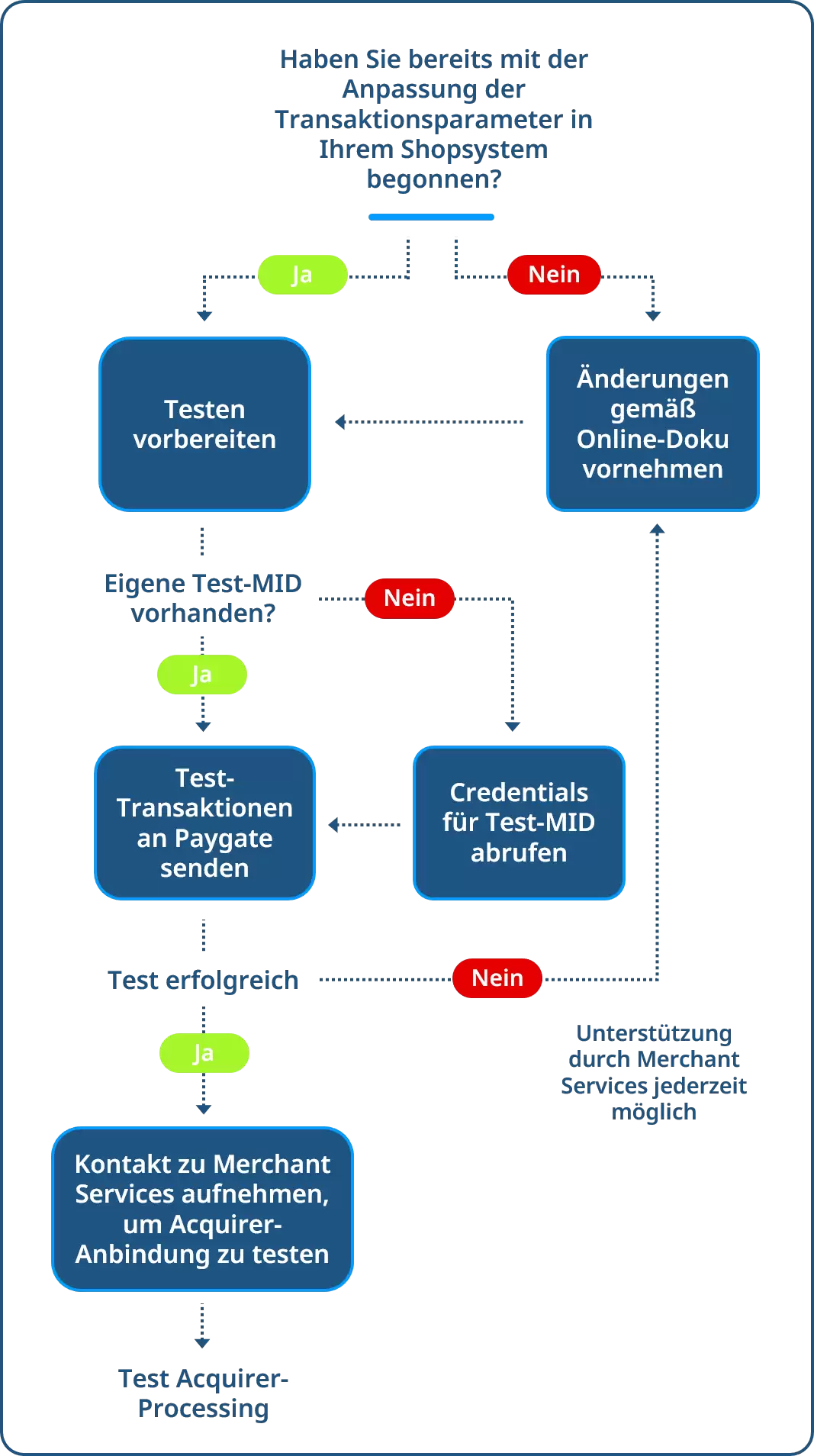
Die Schritte zur Integration von 3-D Secure 2 im Detail:
1. Anpassung der notwendigen Transaktionsparameter
Bitte passen Sie Umfang und Übergabe der Transaktionsdaten gemäß unserer Onlinedokumentation an. Beachten Sie dabei unsere Empfehlungen für die Auswahl der zusätzlichen Datenfelder, deren Übertragung dem Issuer eine optimale Transaktions-Risikoanalyse ermöglicht und somit Ihre Conversions optimiert.
2. Test-MID einrichten
Um die korrekte Datenübertragung an das Computop Paygate zu testen, müssen Sie eine Test-MID einrichten. Falls Sie eine eigene Test-MID bekommen haben (Sie erkennen sie daran, dass im Namen „Test“ enthalten ist), nutzen Sie diese, um Testtransaktionen zu übertragen.
Andernfalls finden Sie in Ihrem Computop Analytics-Account die allgemein gültige Computop Test-MID für 3-D Secure 2. Optional können Sie auch bei unseren Merchant Services eine neue, individuelle Test-MID beantragen.
3. Senden einer Test-Transaktion an das Computop Paygate
Senden Sie unter Verwendung der Test-MID nun eine Transaktion an das Computop Paygate. Wenn Ihre Anpassungen an das 3-DS-Protokoll korrekt sind, erhalten Sie auf Ihre Testtransaktion eine Erfolgsbestätigung.
4. Durchführung des Acquirer-Tests
Mit der Erfolgsbestätigung wenden Sie sich bitte an helpdesk@computop.com. Unser Team wird sich umgehend mit Ihnen in Verbindung setzen, um die weitere Übertragung Ihrer Zahlungen an Ihre/n Acquirer zu testen.
Sollten Sie auf Ihre Testtransaktion eine Fehlermeldung erhalten, überprüfen Sie bitte noch einmal Ihre Anpassung auf Basis unserer Online-Dokumentation. Bei Problemen hilft unser Team Merchant Services gern.